A brute force attack is a method cyber criminals use to easily figure out weak or insufficiently secure passwords. Instead of relying on ingenuity, they systematically work their way through random character combinations and commonly-used passwords until they gain access to whatever it is that they’re targeting. In this article, we’ll let you know what methods they employ and how you can minimize your exposure to their illicit efforts.
Online shops, platforms, and even corporate intranet systems depend on password-protected accounts. As of 2017, the average US internet user had 150 accounts. To gain unauthorized access, hackers frequently resort to rather rudimentary methods: guessing your password. In essence, they try all possible combinations until they hit on a winner.
According to Verizon’s 2021 Data Breach Report, 23 percent of the firms which responded had been targeted by some sort of brute force attack. Once an account has been compromised, cyber criminals often wreak further havoc by carrying out a ransomware attack. And the worst part? Even if they’re not successful in their efforts, you’ll rarely find out, since few platforms are transparent about the number of attacks they’re subjected to.
How Does a Brute Force Attack Work?
When hackers launch brute force attacks, they fall back on trial and error, testing a variety of different character combinations until they hit on the right one. This isn’t carried out manually, but rather, with the help of an algorithm. The amount of time it takes to find the correct ‘key’ depends on the length of the password and the sophistication of the hardware at their disposal:
For example, a four-digit PIN has 10^4 or 10,000 possible combinations. That sounds like a lot, but a modern processor only needs a fraction of a second to generate all of the ‘keys’.
If we take an eight-letter password with upper- and lower-case letters, the number of combinations increases to 52^8. That’s 53,459,728,531,456 or over 53 trillion possible solutions. A high-performance processor would need around seven hours to try all of these.
128-Bit and 256-Bit keys that use encryption algorithms like AES are particularly secure. In hexadecimal notation, these are 32 and 64 characters long, respectively. Even the most powerful known computer would need several sextillion years to go through all of the possible combinations.
Hackers often use specialized hardware to generate keys quickly. ASICs are chips capable of executing certain logical operations faster than conventional processors. Graphic Processing Units (GPUs) are also popular. These chips, optimized for graphics cards, are noted for their extremely high clock frequency.
Potential passwords are generated by a piece of software obtainable on the darknet. There, hackers can also acquire password lists from data leaks in the past or purchase botnets. Just as with DDoS attacks, these networks of external computers can significantly enhance the available processing power at a cyber criminal’s fingertips.
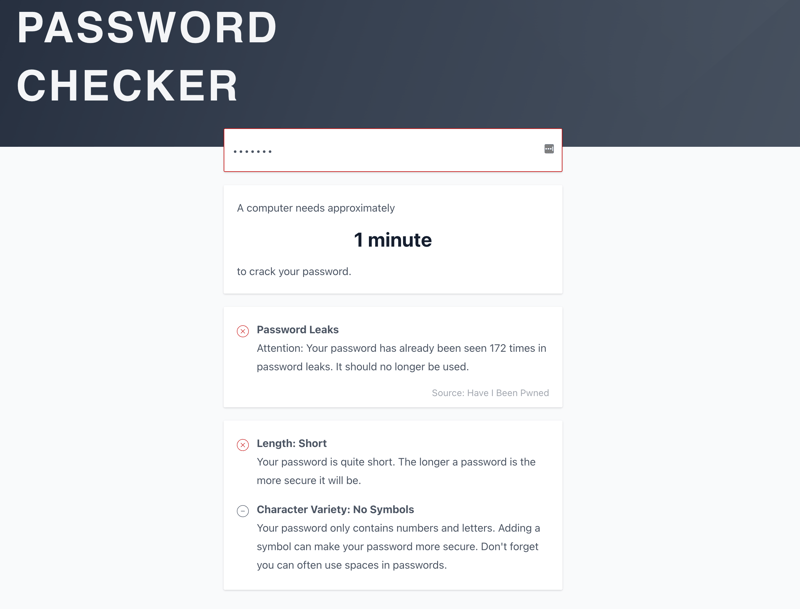
With the EXPERTE.com Password Checker you can find out approximately how long a computer needs to crack a specific password.
Schwache Passwörter, die bekannte Begriffe oder Namen enthalten, lassen sich besonders leicht identifizieren.
What Are the End-goals of a Brute Force Attack?
Just as with phishing attacks and other kinds of cybercrime, hackers launching brute force attacks often pursue multiple goals:
Stealing sensitive data – confidential emails and sensitive financial data can be used to blackmail victims, steal money, or engage in identity theft (such as ordering goods in the victim’s name). If the target is a business, corporate or trade secrets can be stolen and sold to a competitor, which can be particularly lucrative.
Spreading malware – hacked email accounts can be used to send emails with infected attachments or links to fraudulent websites. Recipients are more exposed than would be the case during a regular malware attack, since the compromised email address is likely one that they trust.
Damaging the victim’s reputation – on occasion, social media accounts of officials or organizations are targeted in order to spread false or classified information.
Disrupting operations – cyber criminals can perform brute force attacks to delete data or bring servers to a standstill, either for financial gain or ideological reasons.
Extortion – sometimes hackers combine brute force attacks with other strategies, like ransomware attacks, compromising a password and then using it to gain access to a system. After this, they might encrypt data and demand a ransom for the decryption key.
Gaining control of a website – outsiders acquire login details either through brute force attack or phishing, after which, they could add a banner to the website without anyone noticing. Those who click the banner would inadvertently be supporting the hacker or visit fraudulent websites they had set up.
What Kinds of Brute Force Attacks Exist?
Hackers don’t always limit themselves to random character combinations. Based on the method employed, it’s possible to classify brute force attacks into the following categories:
Conventional brute force attacks – a piece of software generates all possible password combinations, trying each with an account.
Dictionary attacks – attackers use words from a dictionary or password list, attempting to log in with them. During such attacks, they take advantage of the fact that most people rely on well-known words or phrases to make their passwords easier to remember.
Reverse brute force attacks – instead of trying to hack a single account, cyber criminals utilize a single password on thousands of different accounts. Just as with dictionary attacks, simple passwords, like 123456 or qwerty are tested.
Credential stuffing – hackers begin by acquiring a password, such as through phishing. Then, they try the same username and password on other platforms. This is often successful because many people utilize the same login details across multiple accounts.
Hybrid brute force attacks – frequently, brute force attacks combine multiple strategies. For example, hackers can fuse special characters or numbers with passwords from a dictionary. In so doing, they exploit the tendency individuals have to rarely change their password.
Infamous Brute Force Attacks
The public rarely learns about attempted or successful brute force attacks. Nevertheless, from time to time, such attacks do make the headlines:
In a brute force attack carried out against GitHub, a developer platform, in 2013, hackers targeted 40,000 IP addresses using a password list from an earlier data leak. As of the time of writing, it is uncertain how many accounts were compromised.
In 2015, cyber criminals gained access to over 20 million accounts on the website of ecommerce giant Alibaba. Among other things, they bought products and posted fake reviews. Thanks to a password database, 20% of the brute force attacks were successful.
A brute force attack against Nintendo in 2013 lasted for nearly a month. Over 25,000 accounts were affected, with more than 15 million login attempts made in total.
How Can You Protect Yourself Against a Brute Force Attack?
There is no way to prevent a brute force attack. With that said, by employing the correct strategies, users can make it difficult for hackers to ferret out their passwords. IT specialists can also do much to ensure that the servers they are responsible for are as adequately secured against attack as possible.
How To Protect Your Accounts
Strong passwords – choose passwords that are at least 15 characters long. Avoid using actual words, birthdates, or phrases. A password manager makes creating and overseeing secure passwords extremely easy. Find out how strong your password is with our Password Checker.
Secure login – when possible, always log in with two-factor authentication.
Encrypted communications – use encrypted protocols like HTTPS so that hackers can’t intercept your data when you input your password.
Don’t use passwords – methods like FIDO2, which don’t use passwords, are the most secure of all. They allow authentication via biometrics or hardware.
How Administrators Can Protect Their Servers
Limit login attempts – set a maximum number of unsuccessful login attempts. For example, an account could be temporarily locked after three unsuccessful login attempts are made using it. While useful, this won’t protect against a reverse brute force attack.
Change the default ports – Internet applications usually send encrypted communications between the client and server over SSH (secure shell). The default port for this is 22. Knowing this makes it easy for hackers when targeting a server possessing this configuration. By changing the port in the server settings, attackers will need to spend time searching for it before they can get to work. To change the port, open the sshd_config file and change port 22 to a value between 1024 and 65536. Make sure that the port you choose isn’t reserved.
Regulate remote desktop access – many brute force attacks exploit weaknesses in remote desktop connections. Make sure that only specific IP addresses have remote desktop access. Alternatively, you could utilize a zero trust security model, which combines two-factor authentication, firewalls, and geoblocking.
Implement CAPTCHA – using CAPTCHA protects servers by blocking automated bots.
Regularly delete unused accounts – if an account hasn’t been used for an extended period of time chances are high that the login information is out of date and/or no longer meets current security guidelines. Brute force attacks are particularly successful against these kinds of accounts.
Monitor traffic – logs can provide you with an overview of unsuccessful login attempts. Regularly check the logs and block any suspicious IP addresses.
Don’t save unencrypted passwords – passwords on the server should be encrypted with a 256-Bit algorithm. As an added bonus, this doesn’t only foil brute force attacks, it also helps to prevent credential stuffing.
Conclusion
Brute force attacks pose a threat to regular Internet users, server administrators, and businesses. There isn’t a perfect solution, but if you opt for the correct strategies, you can make hackers’ lives extremely difficult.
If you fall in the first category, you can protect your data by employing strong passwords, and, ideally, a password manager. It’s also advisable to look into two-factor authentication or passwordless options. For their part, administrators can keep hackers at bay by correctly configuring remote desktop and SSH connections, setting a maximum number of login attempts, and monitoring traffic.
FAQs
Brute force attacks are attempts by hackers to compromise a password by trying all possible combinations. They either generate random character combinations with a piece of software (classic brute force attack) or use a list of real words (dictionary attack).
Many brute force attacks target SSH or remote desktop connections. This makes it important to log users in using secure authentication methods. CAPTCHAs, limited logins, and blocking suspicious IP addresses all go far in keeping hackers out. Such connections also shouldn’t use default ports.
The longer a password is, the more difficult it will be for an attacker to crack it through trial and error. Using special characters and a combination of upper- and lower-case letters increases the number of possible combinations. A strong password also shouldn’t contain actual words, birthdates, or names. Find out how secure your password is with the EXPERTE.com Password Checker.












