DDoS Attacks - What They Are and How to Guard Against Them
In July of 2021, the IT security service Cloudflare withstood a record-breaking DDoS attack. Hackers bombarded the company with over 17 million requests per second. It wasn’t an isolated case: In 2020 alone, there were approximately 10 million DDoS attacks, and the number of incidents are rising.
The arbitrariness of these attacks is what make them so dangerous. The primary purpose of DDoS attacks is not to steal data; rather, the perpetrators’ goal is to disrupt service and make websites inaccessible. This article covers who is behind DDoS attacks, how they play out, and what you can do to defend against them.
What Is a DDoS Attack?
A distributed denial of service (DDoS) attack is a cyber-attack aimed at rendering a service or server unavailable. Thousands of computers attack the same target by sending messages from different locations at the same time. The server crashes due to the volume of requests, making the website or application inaccessible to legitimate users. Visitors to the affected site often see the error message “HTTP 503 Service Unavailable,” or the page will take an unusually long time to load.
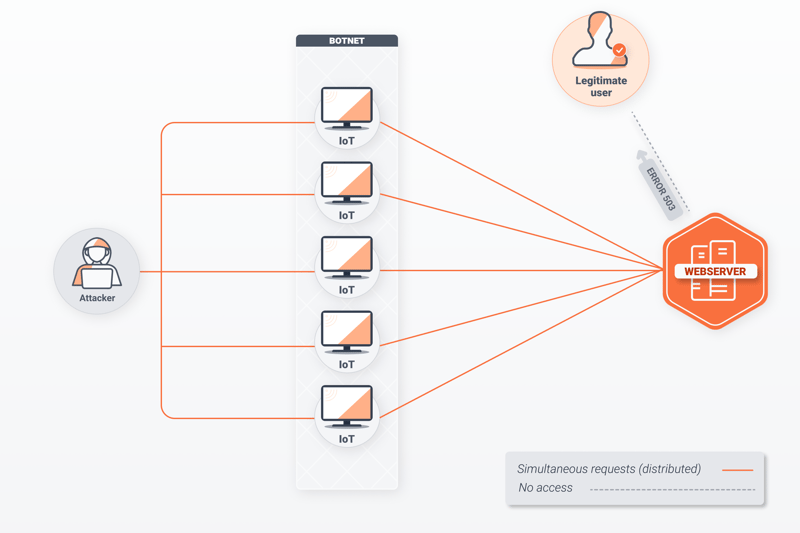
How a DDoS attack works.
The computer network perpetrating the attack usually consists of a group of hijacked devices known as a botnet or zombie network. The owners of these computers likely downloaded malware by mistake and may be unaware that their devices are involved; the attack’s mastermind is often located thousands of miles away.
Over the past decade, devices on the Internet of Things (IoT) with weak security, such as network cameras, sensors, smart TVs, and lights, have been increasingly exploited by hackers for DDoS attacks. However, at present, cybercriminals don’t need to distribute malware to build a botnet; they can simply rent “DDoS as a service” botnets at affordable prices on the dark web.
What Are the Targets of DDoS Attacks?
Botnets attack various layers of network protocols in an effort to exploit a network’s vulnerabilities and bring traffic to a standstill. These attacks usually target businesses— such as platforms, cloud services, or banks. There are various reasons for this, such as:
Shutting down competition: A survey conducted in 2017 revealed that 40% of businesses believed that their competitors were behind DDoS attacks launched against them. A paralyzed IT infrastructure damages a company’s reputation and could see them lose customers.
Blackmail: Hackers often demand a ransom to call off a DDoS attack. They may also threaten a company with an attack if their demands aren’t met by a specific deadline.
Sabotaging organizations or government entities: Some hackers are motivated by ideology, as can be seen when political parties or financial institutions are hit by DDoS attacks. Sometimes government agencies are behind these. For example, since 2000, it has been presumed that North Korea regularly engages in cyber-attacks against its arch-enemy, South Korea.
Distracting IT departments: Hackers have increasingly combined DDoS attacks with other forms of cybercrime, such as ransomware. In such cases, the DDoS attack is used as a diversion. While a company’s IT resources are concentrated on the flood of requests, sensitive data is stolen or malware is smuggled into the organization’s IT infrastructure.
How Is the Strength of a DDoS Attack Measured?
Experts use two parameters to categorize DDoS attacks:
Volume
The amount of data used to flood the targeted system is measured in megabits per second (Mbps), gigabits per second (Gbps), or terabits per second (Tbps). These parameters reflect the amount of data attackers call upon to overwhelm their victims. Although large attacks in the Tbps range have garnered significant media attention in recent years, according to Netscout’s analysis, most DDoS attacks clock in at less than 1 Gbps.Speed
This parameter reflects how fast the bots transmit the data packets. Netscout reports that most DDoS attacks range between 10 and 100 kpps (thousands of packets per second).
How Does a DDoS Attack Unfold?
Almost all Internet applications use client-server architecture. A computer (the client) sends a request to another computer (the server). This happens, for example, whenever you type a web address into your browser.
Servers typically have a bandwidth of several gigabits per second (Gbps), allowing them to process thousands of requests simultaneously. However, issues arise when the volume of traffic exceeds what the server is capable of handling. Think of it as a road during rush hour traffic. Even on the widest highways, the sheer volume of cars can lead to congestion.
Regardless of the technique used, a DDoS attack always follows the same steps:
- 1.
Hackers form a botnet by infecting other computers or IoT devices with malware.
- 2.
Once enough computers are under their control, hackers start the attack by sending a command to each node.
- 3.
The nodes run a script that automatically sends requests to the targeted server. Hackers typically use “amplification techniques,” to generate even more volume than the data packets being sent.
- 4.
If the attack isn’t recognized quickly on the receiving end, the server will either begin to run very slowly, or stop working entirely. For example, users won’t be able to stream videos or payments won’t be processed. A serious attack could even knock the entire website offline.
- 5.
DDoS attacks can last for days. Most hackers won’t stop the onslaught until their demands are met.
- 6.
Most organizations call in a professional to redirect malicious traffic and restore service. This is because DDoS attacks are different from other types of cyber-attacks, where infected files can simply be deleted. The only way to end a DDoS attack is to block the bots and redirect malicious traffic.
What Types of DDoS Attacks Are There?
Internet protocols have several layers, each of which regulates a different aspect of data transport. The OSI model (visualized below) illustrates the process by assigning a specific function to each layer. Depending on the type of DDoS attack, different layers and interfaces can be affected. Accordingly, IT experts group DDoS attacks into the following categories:
Volumetric attacks target bandwidth by generating massive amounts of traffic to the server, exhausting its ability to answer legitimate requests. Volumetric attacks include UDP and DNS floods.
Protocol attacks exploit weaknesses in the network and transport layers (layers 3 and 4 of the OSI model). Servers and firewalls become overloaded with open connections from incomplete or incorrect requests. This category includes SYN floods, ping of death attacks, and smurf attacks.
Application attacks line up the application layer (layer 7 of the OSI model) in their sights, consuming memory and other resources. The most common application attacks are so-called HTTP floods and Slowloris.
Multi-vector attacks don’t belong to any one category. During these attacks, hackers use various gateways into the network and target multiple ports. For example, they may combine both protocol and application attacks. Multi-vector attacks are particularly difficult to guard against; contending with them proactively requires a well thought out, multi-layered approach.
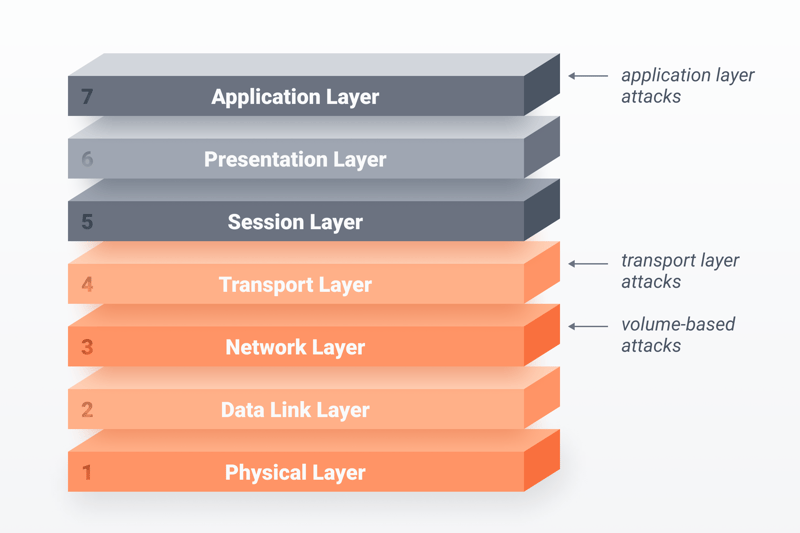
Depending on the type, DDoS attacks target different layers of Internet protocols.
Types of DDoS Attacks - An Overview
Below are examples of specific types of DDoS attacks, along with descriptions of how they work.
UDP Floods
User datagram protocol, or UDP is a connectionless protocol of the transport layer that works without a three-way handshake. During UDP floods, hackers overwhelm a server’s ports with large UDP packets until the server’s bandwidth is completely exhausted. Firewalls often break down because a status message is created for each request. IP addresses are often spoofed during UDP floods.
DNS Reflection
Domain name system, or DNS servers translate URLs into IP addresses using a series of numbers, such as 96.92.212.183. When a user types the website experte.com into their browser, the DNS server responds with the corresponding IP address. During DNS reflection attacks, hackers spoof their victim’s IP address and use amplification techniques to inundate a DNS server with requests. The DNS server replies to the requests, flooding the target with information and crashing the system.
SYN Floods
Unlike UDP protocol, TCP protocol establishes a connection with a handshake. The client sends a SNY (synchronized) message, the server replies with a SYN-ACK (synchronize acknowledge) confirmation, and an ACK confirmation is returned from the client. If the final ACK confirmation isn’t received, the connection will not be established. Too many open requests of this type can cause a server to collapse.
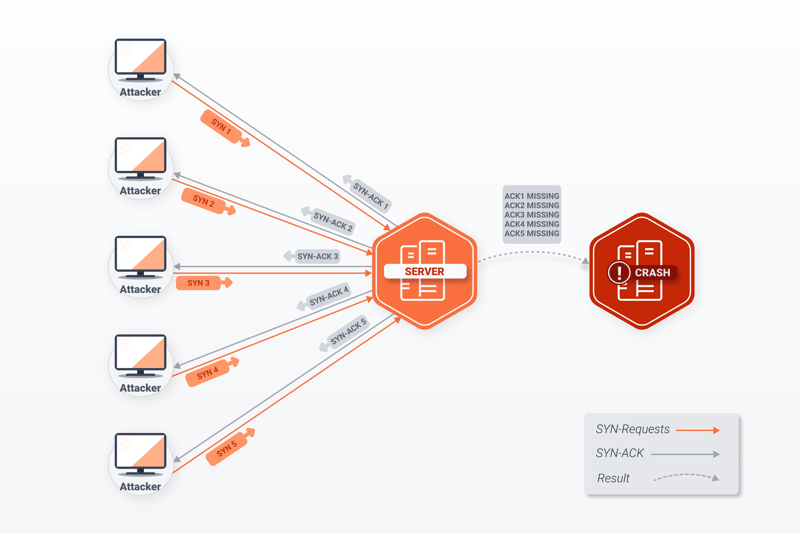
A SYN flood generates enough incomplete requests to collapse a server.
Ping of Death Attacks
The Internet control method protocol (ICMP) is used to diagnose network communication issues within Internet Protocol version 4 (IPv4). This protocol uses, among other things, “pings,” to exchange error messages. During a ping of death attack, a server is flooded with massive packets disguised as numerous smaller packets. The sum of small packets exceeds IPv4’s packet size limit of 65,535 bytes, so when the server attempts to put the small packets together, it crashes.
Smurf Attacks
Smurf attacks also entail bots sending massive numbers of ping packets, however, unlike ping of death attacks, the packets are not faulty. Instead, the ping requests go to the network’s broadcast address with the victim’s spoofed IP address. Every computer in the network responds to the fake requests, generating a spike in traffic on the affected server. The significant number of small attacks, capable of exhausting bandwidth, are what gives this type of DDoS attack its name.
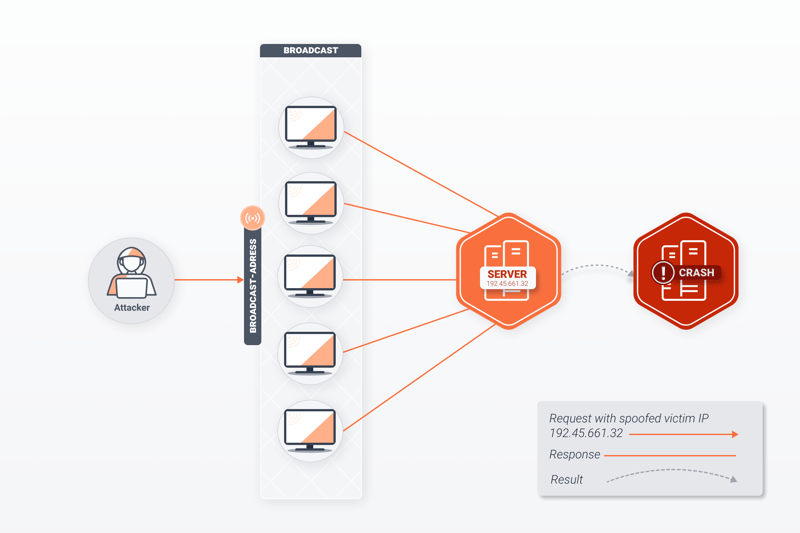
During a smurf attack, the victim is overwhelmed by a flood of messages without having started a request.
HTTPS Floods
Internet browsers such as Chrome or Mozilla operate in the application layer of the OSI model. They send GET or POST requests within the HTTP protocol to solicit static or dynamic data (images or videos) from servers. During an HTTP flood, these bot requests are directed to a server, hindering its ability to respond to requests from legitimate users. Since they’re hard to differentiate from genuine requests, identifying and defending against them is challenging.
Slowloris
Slowloris also affects the HTTP protocol at the application level. Unlike HTTP floods, requests are sent with fake headers. The open connections paralyze the server. Slowloris attacks typically take longer to play out than other types of DDoS attacks, however, they can disrupt traffic for an extended period of time.
Infamous DDoS Attacks
Increased online activity due to the Covid-19 pandemic witnessed a steep rise in DDoS attacks. According to the IT security company F5 Labs, between January and March 2020 alone, the number of DDoS attacks increased by 55%. Below, we've listed some notorious DDoS attacks that have made global headlines:
The world’s first DDoS attack occurred in 1996. Hackers rampaged the New York-based internet provider Panix via a spoofed IP address. They used the SYN flood technique explained above to flood the server with erroneous data packets. Panix’s servers crashed, severing Internet access to customers for 36 hours.
In November of 2016, the European Commission fell victim to a DDoS attack perpetrated by the infamous Mirai botnet. Just a month prior, the same hackers managed to collapse the Liberia’s entire Internet infrastructure by hijacking IoT devices and using them as bots.
September of 2017 saw the largest DDoS attack to date. 180,000 of Google’s servers were inundated by UDP spoofing packets. Despite its strength, Google was able to fend off the attack and made the incident public in 2020.
In February of 2018, a so-called Memcached DDoS attack paralyzed the popular developer platform GitHub. Cybercriminals hacked Memcached servers, which store information from databank systems, and sent requests with spoofed IP addresses. The volume of the requests reached 1.3 Tbps. Despite the scope of the attack, GitHub was able to fend off the flood of data within 20 minutes.
How Can You Guard Against a DDoS Attack?
Because DDoS attacks are highly complex, defending against them requires a multi-level approach. Companies and organizations, in particular, should develop a defense strategy early on to ensure they’re prepared for the worst-case scenario. Successful strategies usually include taking the following measures:
- 1.
Increase bandwidth: When it comes to attacks in the Tbps range, even the largest bandwidth isn’t enough. However, increased bandwidth can be effective at preventing an immediate collapse when it comes to a traffic spike from smaller attacks. Due to their high bandwidth and redundant servers, many cloud services can distribute malicious traffic, ensuring that the application remains available for the majority of genuine users.
- 2.
Properly configure firewalls and routers: Firewalls and routers can be set to block invalid IP addresses and to have low thresholds for UDP, ICMP, and SYN packets. However, these settings mean little if the hackers use spoofed IP addresses. A countermeasure called black hole routing discards all packets into a “black hole.” This is particularly helpful when protecting a handful of affected servers within a larger network.
- 3.
Monitor traffic: Unusual spikes in traffic are one of the first signs of a DDoS attack. Once the malicious source is identified, traffic coming from that address can be redirected.
- 4.
Adopt a zero trust security model: Choosing a zero trust security model reduces the likelihood that your network will be hijacked for DDoS attacks. While it doesn’t ward off attacks aimed at your organization, it will deprive hackers of potential resources to commit DDoS attacks against others. This approach includes two-factor authentication for the local network and VPN services, as well as anti-spam filters, firewalls, and anti-malware software. Other possibilities include geoblocking for restricting requests from specific regions. However, that would also exclude legitimate visitors located in those countries.
- 5.
Choose a provider with good DDoS protection: ISP redundancy means that in the event of an attack, one Internet provider's customers will be redirected to another, ensuring that their website remains available.
Conclusion
DDoS attacks will continue to be one of the biggest cyber threats well into the foreseeable future. That the masterminds behind these attacks use hijacked computers, makes them difficult to prevent or protect against. As such, the best counter to DDoS attacks is creating resilient IT systems that can quickly identify and redirect malicious traffic.
FAQs
DDoS attacks see hackers flood unsuspecting servers with data packets. They do so using a bot network, which often includes computers located all over the world. The victim's website becomes inaccessible because their servers can no longer process or address legitimate requests.
Hackers are motivated by anything from financial gain to a desire to harm a company or institution for ideological reasons. There is typically a ransom demanded to bring the attack to a halt. Sometimes DDoS attacks are combined with ransomware attacks or are used to distract an IT team while sensitive data is stolen.
Because DDoS attacks usually take place across several vectors, it’s important to embrace a multi-level defense strategy. Among other considerations, you should immediately identify and redirect any suspicious traffic. It also helps to properly configure your router so that erroneous packets are dropped the moment they are received.













