When surfing the web, computers, smartphones, and devices transmit lots of data, including your IP address. Anyone who knows how can easily determine your location and eventually, identity. Although most of the time, this information is collected for marketing purposes, hackers, your employer, and even governments can use it to spy on you.
It's normal to want to conceal your IP address. You'll be able to bypass geo-blocking and access websites or content that would otherwise not be available in your actual location. Streaming services, in particular, offer different content catalogs and subscription prices from country to country.
In this article, we'll explain how you can hide your IP address, and how much anonymity this actually provides.
Hide Your IP Address With a VPN
One of the most popular ways to conceal your online identity is with a virtual private network (VPN). These closed networks allow data to be encrypted and sent anonymously across the web.
The easiest way to get started with a VPN is by purchasing a subscription from a reputable provider. Once connected, you can change your IP address to that of the VPN server and create a secure tunnel between you and the server. Your target (a website, for example) will only see the VPN server's IP address but not your device's.
The site you're visiting then responds to the VPN server's request with the desired data. All traffic between you and the VPN server is encrypted, adding extra security that protects you from prying eyes.
Apart from these benefits, VPN software often includes additional functions or features that further enhance your digital security. For this reason, companies, organizations, and even government authorities use VPNs to shield their staff when remotely accessing programs or information.
These days, there are many VPN providers, some of which offer thousands of servers all over the world. By connecting to one, you can bypass pesky geoblocking and stream content from practically anywhere, even places where it isn't available.
Often, all you'll need to get started with a VPN is an email address. Some services even allow users to completely anonymize their accounts and pay for subscriptions with Bitcoin, or cash in an envelope. All providers promise not to save logs or to give data to third parties, however, we check whether you should take them at their word in our reviews.
Anonymous Surfing With a Browser Plugin
Should you only want to anonymously surf the web, and not use other programs or clients, VPN browser plugins can lend a hand. These don't just encrypt all of your browser activity but simultaneously conceal your IP address. There are plenty of useful options, like Hotspot Shield's free VPN proxy* or ZenMate's free VPN* for both Mozilla Firefox and Google Chrome.
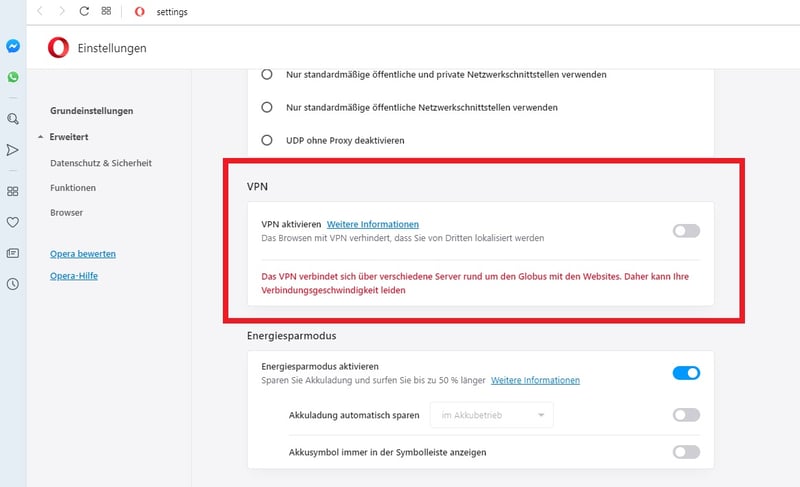
Opera comes with an integrated no-limits VPN service. In contrast to other VPN apps, you don't need to register separately but can activate the VPN through the settings menu. Once there, select a virtual location for your connection, or be automatically assigned a random one. Unfortunately, unlike most VPN apps, it isn't possible to specify a country, but only a region (Asia, North America, or Europe).
Another drawback: Opera's integrated VPN won't help to stream multimedia content from abroad since its IPs are already known and blocked by streaming platforms.
Plugins are not for everyone. Many believe that they're just another means of collecting personal data. Keep in mind that the secure tunnel you've created only protects your browser. This means that while your surfing is anonymous, other applications can still see your "real" IP.
There is a common rumor that VPNs throttle connection speeds. In reality, the difference between VPN and non-VPN connection speeds owing to the former's extra encryption isn't too significant (less than 5% of the maximum total bandwidth).
Hide Your IP With a Proxy Server
A proxy server is an intermediary that handles client-server communication when you request a website. Your requests are accepted with your IP but then forwarded to the destination with a new IP address from the server. The response is then returned to the proxy server, and back to you. In this manner, the sender remains anonymous, and no direct connection exists between the requester and the destination.
Proxy servers only need to be configured once in the client's network settings, after which all Internet traffic will be routed through them. This approach also allows regional content restrictions to be bypassed. In contrast to VPNs, however, data traffic isn't encrypted, making it less secure. As such, proxy servers don't offer a comprehensive way to hide IP addresses.
TOR: A Special Kind of Proxy
For most, "the onion routing project" (TOR) sounds weird or dangerous. Some might even associate it with the so-called Darknet. Originally, TOR was used by the US Armed Forces to clandestinely communicate with the rest of the government. This helps explain why it isn't through the regular Internet.
Just like an onion, the TOR network is composed of multiple layers. Users access it through an encrypted TOR client, which is little more than a modified version of Mozilla Firefox.
The "entry node" can be any TOR server from a random list that loads when accessing the client. To do this, the client sends a request to a selected node, from which the data packet is then forwarded to the next node until it reaches its destination. Each node only knows the one that preceded and follows it, but not the source, or exit node, which never receives the user's IP address.
However, even on the TOR network, you aren't entirely anonymous, as the system has two weaknesses:
Not all connections through which a data packet is transferred are encrypted, particularly when traveling from the client to the entry node. Total security can only be guaranteed if you manually configure SSL/TLS encryption for your browser, or connect to TOR using a VPN.
Alongside private administrators, a number of nodes are managed by state authorities. Should an exit node be operated by one of these, all of your network traffic will be visible.
In addition, TOR only partially disguises the sender's IP address, but not the application (client) or the browser's digital signature.











