According to Forbes, around 15 billion stolen passwords are circulating around the Darknet. Even long ones comprised of random characters aren't secure if cybercriminals are able to find them where they've been saved. Password hashing algorithms enhance security by translating each password into a code that can't be decoded in reverse. In this article, we'll explain how password hashing works and what you should keep in mind when using this technique.
What Is Password Hashing?
Whenever you open an account with an online shop, the website saves the password you've chosen on its server, often even locally. However, the need to store this data carries risks; if the server is hacked, cybercriminals can easily gain access to passwords.
Some websites store all of their passwords in encrypted form. While this certainly improves security, it's only partially effective against hackers. Here's the problem: an encryption algorithm needs a key to decrypt the data. Since the key is also kept on the server, it's vulnerable to misuse in the event of a data breach.
Password hashing methods, in contrast, convert the password into a "string" (character sequence) with a fixed length. As an example, qwerty translates to 65e84be33532fb784c48129675f9eff3a682b27168c0ea744b2cf58ee02337c5 using the SHA-256 algorithm. This code is a sequence of 64 hexadecimal characters, with each character requiring 4 bits of memory.
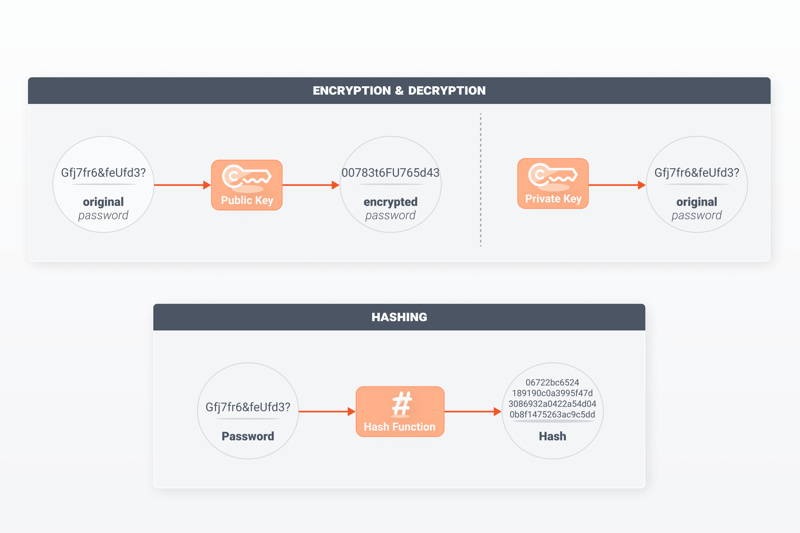
With encryption, your private key is still stored on the service's server, however, with hashing, the website only keeps the final hash.
Unlike encryption, the algorithm operates in one direction only (the so-called, one-way function), making it impossible to derive the original password from the string. In a sense, hashing works like a fingerprint. You can compare fingerprints and match them to individuals. However, it's impossible to determine someone's identity from a fingerprint if their information isn't already stored in a database.
You can use this online tool to see how different algorithms from the SHA and Keccak cryptographic families convert words and phrases into hash.
How Does Password Hashing Work?
Here's what happens when you log in to a website that uses password hashing:
- 1.
You create a password during your initial login. The website hashes it and stores only the hash.
- 2.
The next time you log in, you enter the unencrypted password.
- 3.
The hash function again calculates the hash and compares it with the stored one.
- 4.
If the hash values match, you will be logged in.
- 5.
If you lose or forget your password, you'll have to generate a new one via an email link or other method (e.g., text message). The website cannot recover the old password from the stored hash.
What Makes a Good Hash Function?
There are numerous hash algorithms, with the earliest dating back to the 1970s. Since then, many more have been created, however, all of these algorithms share the following properties:
One-way function - With a one-way function, the argument cannot be calculated based on the function value. For example, let's try hashing the sentence, "The sun is shining", using the SHA-256 algorithm. The result is c4512d108926769997cd2abe3e3cb8f13f35363d8c0353b66a0d889986245e7c. It's impossible to determine the original sentence from this string.
Deterministic - If we enter our example sentence into the hash tool several times, we always get the same result. This ensures that if you enter the correct password, you'll always be able to log in. That being said, a slightly different entry, such as, "The son is shining", will result in 7c06434c82c9a4116a1aba38fe2bfc93e2ccbf622f61a445e57f210c7d4e4829, which is a completely different string of characters. For this reason, brute force attacks (where hackers attempt to suss out passwords by using multiple variations of them) lose their potency.
Results with the same format - With the SHA-256 hash function, all input—regardless of length—results in a 256-bit string. Generally speaking, all passwords hashed with the same algorithm have the same length, regardless of what the original password is.
Collision resistant - Two different inputs should never produce the same result. In practice, no hashing algorithm is 100% collision-resistant, because while the input values are infinite, the number of outputs is at most a^b (a = the number of possible characters; b = the length of the string). However, this is still sufficient, as the probability of collision is extremely low.
Common hash functions that provide high security include SHA-3, SHA-256, and SHA-512, as well as BCrypt, PBKDF2, Argon2, and Scrypt.
What Does It Mean to Add Salt and Pepper to Your Passwords?
Even password hashing doesn't prevent all unauthorized access. According to a study by cybersecurity experts ID Agent, millions of people use their number-one sports team, favorite band, or common first names as account passwords. Hackers can simply browse through their victims' social media accounts and start guessing passwords. Cybercriminals will also hash a popular term along with slight variations and then test the results on hundreds of thousands of accounts (known as reverse brute force attacks).
To solve this problem, some websites add a string to each password before hashing it. These are known as salted passwords. Like the hash, the salt is stored on the server. There are unique salts, where each user has a unique string, and salts that are applied to all users. The former provides a higher level of security.
Pepper works in a similar way; it adds a string to the original password. Unlike salt, pepper is not stored in the website server database but is hard-coded. This means that even in the event of data theft, accounts will not be compromised. On the other hand, the same string is used for all passwords, making them easier to guess.
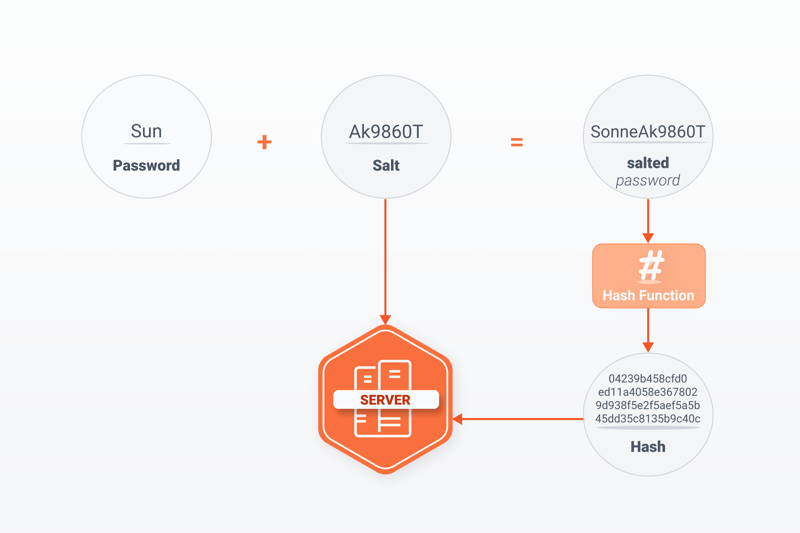
Both the salt and hash are stored on the server.
Is Password Hashing 100% Secure?
Even salted and peppered passwords along with the best hashing algorithms don't offer complete protection. Hackers can still achieve their goals by pursuing the following strategies:
In classic brute-force and dictionary attacks, hackers generate millions of hashed passwords and compare them with the hash values stored on the server. If two match, they will have identified the original password.
On the Darknet, criminals sell tables with pre-generated or stolen hash values exactly for this purpose. These "rainbow tables" enable a structured search for the password matching a particular hash, and are much faster than brute force attacks.
Even salted passwords aren't completely secure; in the event of data theft, the salts themselves can fall into the hands of cybercriminals.
Conclusion
Password hashing is a common way to keep passwords secure on servers. Even in the event of a successful server attack, hashing algorithms ensure that hackers only receive worthless strings. Salting and peppering passwords enhance security even further.
However, if the passwords can easily be guessed, brute-force attacks on databases can have more devastating results. Hackers have also cracked some hash algorithms. In the end, strong passwords and up-to-date algorithms offer the best protection against data theft.











