Tor and Tor Browser: Anonymity on the Web?
"Use Tor," Edward Snowden once suggested to FBI employees on Twitter to protect their private conversations. Snowden knows what he's talking about: His revelations about US intelligence surveillance practices forced him into exile. Privacy advocates want him to receive the Nobel Peace Prize for his revelations - while opponents call for the death penalty.
Tor can be a matter of life and death for journalists or government critics who use it to encrypt their messages in authoritarian states. But it's also useful for anyone who cares about privacy and data protection to know about different options for online anonymity. And few programs anonymize as well as Tor.
What Is Tor?

Tor, short for "The Onion Router," was originally developed for the US Navy to keep their communications secret. It's a program that makes your internet activity anonymous by routing your data through a network of connection points called Tor relays.
Imagine you want to send someone a letter. You write your message and address on the envelope, but instead of mailing it directly, you put it in a lockbox that only one person has the key to.
You then put this box inside a bigger box that only another person can unlock. You repeat this process several times. Your letter and its message are now protected by multiple layers using asymmetric encryption - like the layers of an onion.
This is basically how Tor protects your online communication.
The term "Tor" is used for different parts of the same system, which can be confusing. But it's actually quite simple:
Tor is the name of the program itself.
The Tor Network is the network of Tor relays run by volunteers worldwide.
The Tor Browser is basically a version of Mozilla Firefox that's set up for maximum privacy.
The browser is the most well-known Tor component, and it's usually what people mean when they talk about Tor.
Difference Between Tor and VPN
Tor isn't the only way to hide your internet traffic. You might already be thinking of another three-letter acronym: VPN (Virtual Private Network).
A VPN routes your traffic through encrypted third-party servers to protect your privacy. Unlike Tor, which uses a large network and encrypts data through multiple layers, each VPN is a single company you need to trust.
Since there are many VPN providers with different features and quality levels, it's hard to make a direct comparison between these two privacy methods. However, there are some key differences to consider when making your choice.
Tor | VPNs | |
|---|---|---|
Cost | free and ad-free | usually paid, free VPNs have limited features |
Speed | slower than VPNs due to layered structure | faster than Tor (check our VPN speed test) |
Encryption | Strong encryption of your IP address through multiple nodes | Good encryption but usually through one node (some VPNs offer multi-hop features) |
Ease of use | similar to Firefox and easy to use | user-friendly VPN apps |
Browser dependent | Yes: you need to use the Tor browser for all online activities | No: VPN connection works outside the browser |
Security | High, since Tor is run by a large network of volunteers | Depends heavily on the provider |
Extra features | None | Useful extras - like bypassing geoblocking for streaming |
So Which Should You Choose - Tor or VPN?
For highly sensitive communications - like those of journalists, whistleblowers, or political activists - Tor is likely the best choice. A VPN also helps hide your online activities, but it's most useful for getting around regional blocks: you can unlock streaming content from other countries or bypass China's Great Firewall.
You can also use Tor and VPNs together. This can boost security even more - but comes with its own challenges.
Tor isn't the only browser focused on privacy and security. While none of its competitors have Tor's extensive "onion routing" network, it's worth checking out our big privacy browser comparison.
How to Use the Tor Browser?
If you want to protect your internet traffic with the Tor Browser, you can download it from the Tor Project website. It's available for Windows, macOS, and GNU/Linux in 25 languages.
Step 1: Visit the Tor website and choose the right download for your operating system.
Start the download.
Step 2: Pick a folder to save the Tor files and install the program like any other software.
Install Tor.
Step 3: Open the program you just installed. If you need to adjust any settings, like using Tor with a proxy server, click "Configure." Usually, you can just click "Connect" to access the Tor network.
Now you just need to connect.
Step 4: When starting Tor, you'll need to wait a bit while the browser connects to the network. The first time might take a few minutes, but once connected, the browser opens quickly.
Since the Tor Browser is based on Mozilla Firefox, it's easy to use.
Step 5: In the security settings, you can find the right balance between privacy and functionality. By default, the Tor Browser is set to the lowest of three security levels (which still offers much better protection than regular browsers). Higher levels may limit JavaScript and HTML5 media.
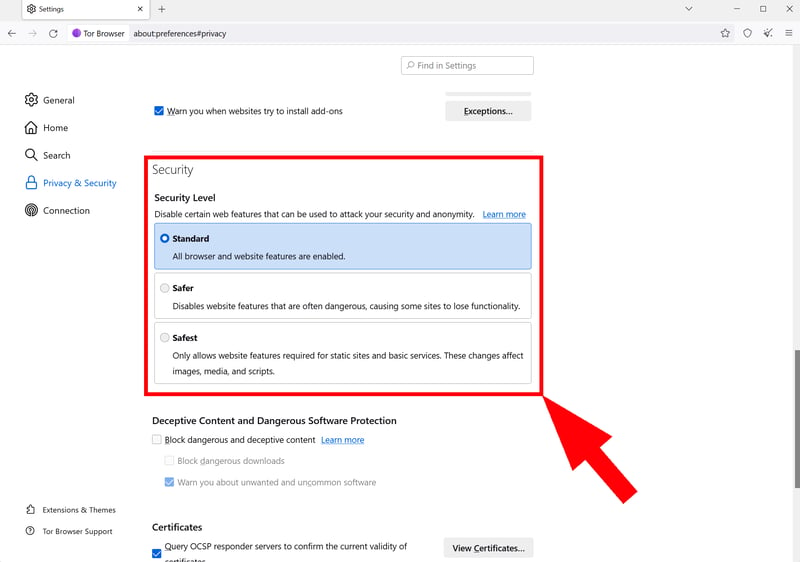
Choose a security level.
Conclusion: Tor - More Than a Browser
Tor is a network that makes your internet traffic anonymous. When you browse with Tor Browser, your data is routed through multiple servers worldwide and encrypted, making it nearly impossible to track your activities. That's why Tor is essential for many activists, journalists, and whistleblowers who need to protect their communications.
However, if you mainly want to hide your IP address or bypass geo-blocks to access streaming services or get around internet censorship, a VPN might be enough.














