Tor Alternatives: 4 Other Methods to Surf Anonymously
More than two million people use Tor to surf the internet anonymously every day. But Tor isn't the only way to protect your privacy and avoid censorship online.
Depending on which Tor features are most important to you, there are a few alternatives worth considering. This article draws attention to Tor's disadvantages and suggests other programs you might want to use in its place.
Tor browser is your ticket to Tor's network.
Tor's Disadvantages
To start, it's important to discuss why you would look for an alternative at all. Despite its popularity, Tor does suffer from a few weaknesses and disadvantages, namely:
Tor is often slow
Tor works hard to keep its users anonymous. It routes your connection through multiple servers in different locations, but this comes at the cost of connection quality and speed. You surf significantly slower with Tor than without it, readily apparent in long loading times or choppiness while streaming videos.Tor is not 100% anonymous
Simply using Tor doesn't guarantee 100% anonymity or protection from tracking. Instead, your degree of privacy depends on what you do while using Tor; for example, if you log into your Facebook or social media account in Tor browser, your behavior can still be tracked. You could also run into a malicious exit node. While exit nodes cannot identify you, they are able to access data you send.Tor users are considered suspicious by governments
Tor isn't just used by people like Edward Snowden and Julian Assange; it's also popular with criminals who want to cover their tracks. As a result, governments and security agencies—especially the NSA in the United States—are skeptical of Tor users in general.Slow startup
When you open Tor browser, you'll have to wait a few seconds before you can begin, since it needs to connect to Tor's network.Tor is blocked in some countries
Some countries, such as China, Russia, and Iran, have completely blocked Tor's network. It's important to be especially careful in these regions since authoritarian governments are even more skeptical of Tor users.Tor doesn't protect against malware
While it can be used to download files anonymously, Tor doesn't protect against Malware. This means that your system can still be infected by viruses or trojans when downloading via Tor's network.Dangers lurk on the Darknet
Tor gives you access to the Darknet. While there's plenty of legitimate content to be found there, it's also home to all sorts of criminal activity. Be careful what you do and which websites you visit on the Darknet.
Top 4 Alternatives to Tor & Tor Browser
Finding out which Tor alternative is best for you depends on your priorities and goals. Below are four alternatives along with their pros and cons.
Tor Alternative #1: VPNs
A VPN also ensures privacy by routing your Internet traffic through a server, which acts as an intermediary. Your connection thereafter enjoys encryption and your IP address is masked, which means that no one can track you on the Internet. VPNs also allow you to bypass geoblocking while streaming and gain access to foreign Netflix content catalogs.
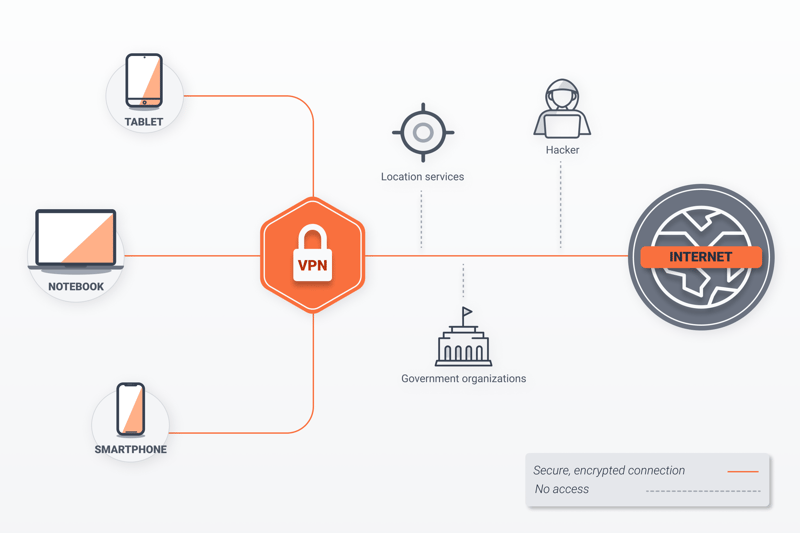
A VPN stands between your devices and the Internet.
While VPNs work using a similar principle as Tor, there are some differences:
A VPN typically routes your traffic through only one server. This means that connections via VPN servers are often much faster and more stable than those made through Tor. As a result, VPNs are more conducive to video streaming and other activities that require large amounts of data traffic.
There's only one Tor network, which is operated by a worldwide community of volunteers. In contrast, there are numerous VPN providers, each of which runs its own network of servers. While most providers promise not to log user data, you're still entrusting your data to a private company, which isn't the case when using Tor.
Tor can only be used on Windows, macOS, Linux, and Android, while VPNs are available for numerous platforms, including routers and smart TVs.
With just a click of your mouse, VPNs provide access to servers all over the world. In Tor browser, this feature must be set up manually, which is a bit cumbersome. Therefore, if you want to bypass region restrictions or access content from certain countries, it's best to use a VPN.
VPNs are typically paid services, but there are also free versions that come with certain limitations.
Want to surf anonymously, but aren't ready to compromise on speed.
Would like to easily bypass geoblocking, such as accessing foreign streaming content or viewing media libraries from back home while on vacation.
Need to frequently and reliably circumvent censorship measures (for example, when traveling to China).
Are interested in protecting your privacy while on public WiFi.
In our EXPERTE.com VPN comparison, we put 22 VPN services to the test. Here are our Top 3 picks:
NordVPN — EXPERTE.com's Review Winner

NordVPN is our best in show when it comes to VPNs. This Panama-based service combines user-friendliness, security, and speed into an excellent overall VPN package. Its network is impressive, with over 5,000 servers available in 58 countries. NordVPN also took first place in our speed test, which we regularly use to measure VPN providers' upload and download speeds.
NordVPN provides an array of features, including split tunneling and malware protection. The service also has an intuitive and stylish interface that makes it ultra-simple to use.
ExpressVPN

ExpressVPN is a good VPN overall. It offers top speeds, a large, 94-country server network, and user-friendly apps. We like ExpressVPN's browser extension and consider it the best VPN tool of its kind for Chrome and Firefox.
However, ExpressVPN is significantly more expensive than other providers. This is especially true if you compare its rates to the inexpensive long-term plans offered by its competitors.
Surfshark

Surfshark, on the other hand, is one of the least expensive VPNs on the market; their 24-month plan costs just one-third the price of ExpressVPN's. Surfshark isn't just our price-performance ratio winner though, since it also scored well in other areas. We noted excellent upload and download speeds during our test, the plenty of features to choose from, and the program's security, verified by external audits.
Tor Alternative #2: P2P Network for the Darknet
Dedicated P2P networks are an alternative for those who primarily use Tor to access the Darknet. These offer access to a "separate" Internet that functions independently from the World Wide Web.
Primarily want to access the Darknet and are looking for a dedicated service to do so.
Know what you're doing; you should have the IT skills to manually set up and properly configure the necessary tools.
There are several programs to choose from, including:
I2P — The Invisible Internet
I2P (The Invisible Internet Project) is like a replacement for the "normal" internet and can be thought of as a self-contained Darknet. It's a decentralized network that functions according to the P2P principle; every user on the network turns into a node, and each connected device acts as a router. However, none of the nodes can read any data sent through the network.
The program also aims to protect its users' privacy and anonymity, but, unlike Tor, it's a closed network. This means that data always remains within the I2P network and you won't find it on public servers (where it could be intercepted by entities such as security services).

I2P welcomes you to the "invisible internet".
There are several differences between Tor and I2P:
While Tor allows you to access the regular Internet, I2P was designed specifically for the Darknet. As such, you'll need special Java-based software to write emails, download torrents, or visit anonymous websites on the I2P network (so-called eepsites).
In addition to onion routing, which is used by Tor, I2P also relies on "garlic routing", which makes the service a bit more secure. With each request, I2P sends several data packets that pass through different nodes. This traffic is one-way and routed through a different tunnel each time. When you use Tor, on the other hand, incoming and outgoing traffic always passes through the same nodes. As a result, in terms of privacy, I2P is slightly more secure than Tor.
The I2P app is available for Windows, Linux, Debian/Ubuntu, and Android, but not for iOs.
I2P must be manually configured, unlike Tor's app, which can be downloaded and used out of the box.
ZeroNet — The BitTorrent-Based Network
Built around the same concept as I2P, ZeroNet is like a parallel internet; instead of websites being hosted on one or more servers, they're hosted on a P2P network. Each ZeroNet page is identified by a unique public key (made using Bitcoin cryptography BIP32) as opposed to an IP address.
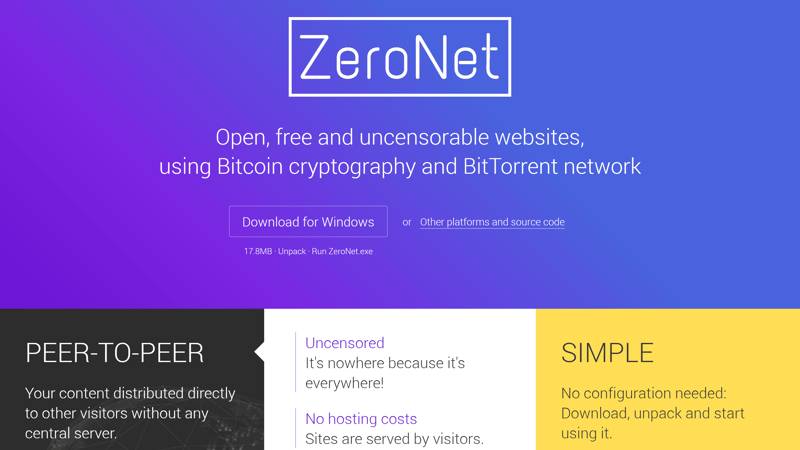
ZeroNet is a P2P network based on BitTorrent.
ZeroNet also has a few special features compared to Tor:
By default, ZeroNet is designed for anonymous data transfer, however, it also has a built-in feature that allows you to use Tor encryption.
You don't need a special browser for ZeroNet. You can simply download and activate the ZeroNet application and use your regular browser.
ZeroNet is based on BitTorrent. Similar to BitTorrent, websites in the ZeroNet network are "seeded" by users, making them free, always accessible, and safe from censorship.
Tor Alternative #3: Privacy Browsers
Tor isn't just a network; it's also a browser that uses Tor's network. However, Tor isn't the only browser on the market that offers security and anonymity. A number of "privacy browsers" that are more privacy-conscious than Chrome, Internet Explorer, and other well-known browsers also exist.
Privacy browsers are modeled after "classic" browsers, but offer additional security features and enable some data protection and privacy settings by default.
Desire a certain level of anonymity while browsing but don't want to sacrifice speed.
Want to protect yourself from tracking and cookies.
Would like to keep your activities unknown to others using the same device.
There are countless privacy browsers available, including:
Brave
Brave is a privacy browser based on Chromium, just like Google Chrome. When using Brave, tracking is blocked by default and you're protected from browser fingerprinting as well. It's also possible to further configure your security settings in the browser to your individual needs.
Brave functions like a conventional browser, staying away from extravagant encryption principles or onion routing like Tor. This means that you'll surf much faster using Brave than you would with Tor browser.

Compared to conventional browsers, Brave is ahead of the curve when it comes to privacy.
Epic Browser
Epic Browser is another privacy browser that promises more anonymity on the net and is also based on Chromium. It doesn't collect any data about its users, and you automatically surf in "incognito mode".
With Epic Browser, no page history is saved, all data is automatically deleted at the end of each session, and tracking is blocked. Other features that may compromise your privacy, such as autofill, search history, and plug-ins, are blocked automatically.
Epic is among the most popular privacy browsers.
Tor Alternative #4: Proxy Servers
A proxy server also redirects your traffic to intermediary servers. It forwards your requests to the websites you visit and sends them back to you, which means you don't directly come into contact with the websites you visit. As a result, websites cannot obtain information such as your location or ISP, because you're using the proxy server's IP address.
Proxy servers also have special characteristics compared to Tor (and VPNs):
Proxy servers mask your IP address but don't encrypt the connection. While they provide a certain degree of anonymity, they can't compete with Tor in this regard.
Proxy servers don't affect connection speed to the same extent as Tor, though performance depends heavily on which proxy server you use.
You don't need to download an additional program; simply configure the proxy settings in your operating system or browser.
There are both paid and free proxy servers. Free proxies are often unreliable or slow.
There are also simple web proxy services that allow you to quickly and easily connect to a specific website by proxy. This is especially practical if you just want to bypass a particular region restriction.
Want to bypass certain region restrictions as easily as possible.
Would like to hide your IP address, but can do without encryption of your traffic.
Privacy isn't your #1 concern.
If you're looking for more information about proxy servers, check out our EXPERTE.com guide: Proxy Meaning Explained: What Is a Proxy Server?
We've also compiled an up-to-date list of free proxy servers here:
Conclusion
Tor isn't the only tool that promises more anonymity and privacy on the Internet. Depending on what you'd like to accomplish online, you do have some other options.
VPNs are handy tools with which you can encrypt your connection. They'll mask your IP address for anonymous surfing and help you bypass geoblocking as well, with little sacrifice on your part when it comes to performance. VPNs are particularly well-suited for video streaming.
Proxy servers are practical if you just occasionally need to bypass geoblocking on websites to access specific content online.
If you need access to the Darknet or want to communicate safely and freely away from the regular WWW, P2P networks are a viable alternative.
To prevent tracking with a browser that's a bit more security-conscious than the rest, it's worth considering a privacy browser.











